OWASP Smart Contract Top 10 2025
The OWASP Smart Contract Top 10 2025 is a comprehensive awareness document for Web3 developers and security teams, focusing on the most critical vulnerabilities in smart contracts and blockchain applications. In 2024 alone, over $1.42 billion was lost across 149 documented incidents due to these vulnerabilities.
Evolution from 2023 to 2025
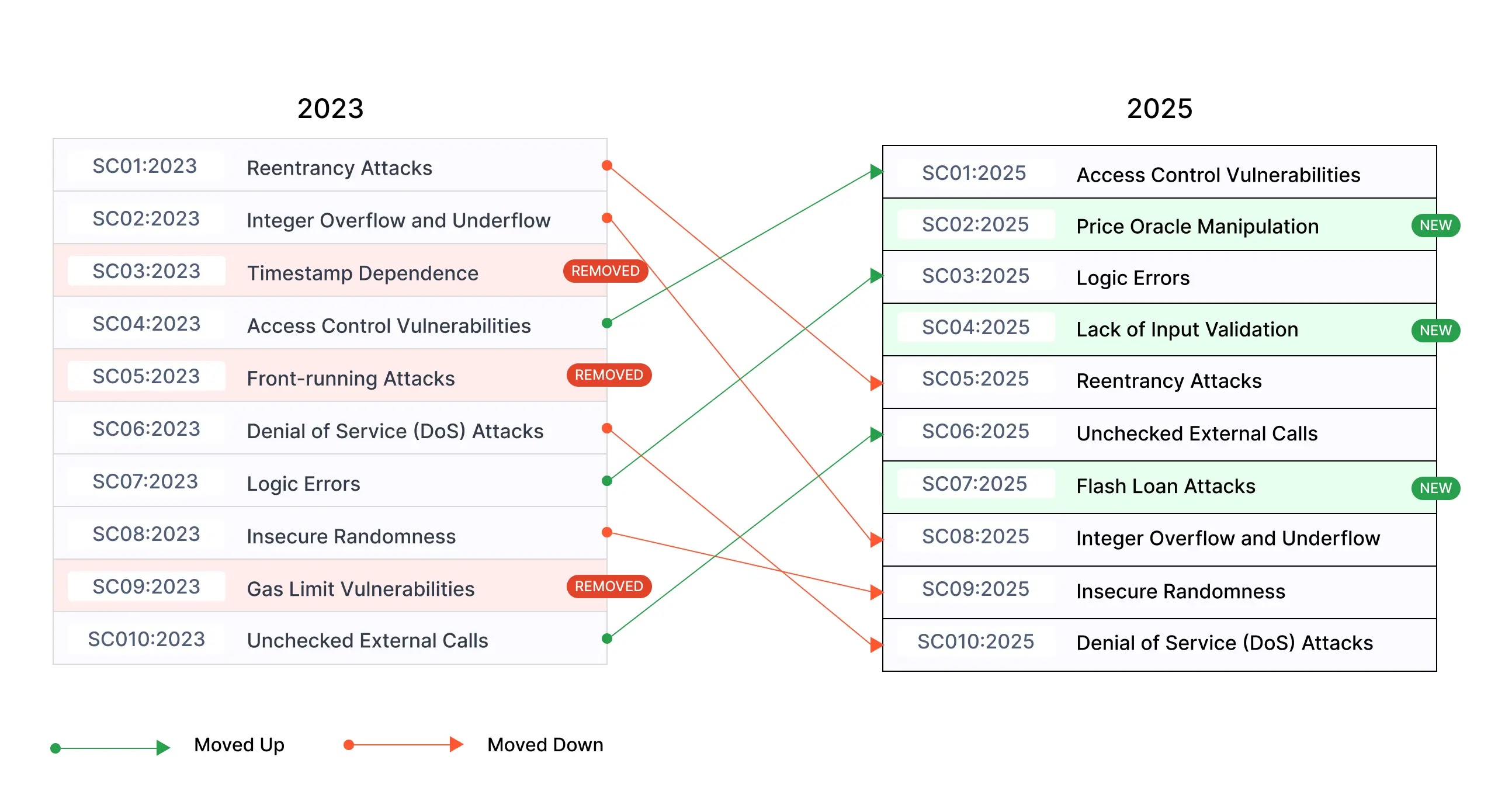
REMOVED Timestamp Dependence, Front-running Attacks, Gas Limit Vulnerabilities
2024 Impact Statistics
0
Total Losses
$1.42B across all vulnerabilities0
Documented Incidents
Verified security breaches0
Access Control Losses
$953.2M from AC vulnerabilities0
Logic Error Losses
$63M from logic flawsAccess control flaws remain the leading cause of financial losses in smart contracts, accounting for $953.2 million in damages in 2024 alone. These vulnerabilities occur when permission checks are improperly implemented, allowing unauthorized users to access or modify critical functions or data.
Example: The 88mph Function Initialization Bug allowed attackers to reinitialize contracts and gain administrative privileges.
Manipulating price oracles—external data feeds used by smart contracts—can destabilize protocols, leading to financial losses or systemic failures. Attackers often exploit poorly designed oracle mechanisms to inflate or deflate asset prices temporarily.
Business logic vulnerabilities arise when contracts fail to execute their intended functions correctly. These errors have led to significant losses ($63M in 2024) through various attack vectors:
- Improper token minting mechanisms
- Flawed lending protocol implementations
- Incorrect reward distribution calculations
- Faulty state transition logic
These vulnerabilities often result from complex business rules being incorrectly translated into smart contract code, leading to exploitable inconsistencies in contract behavior.
Failure to validate user inputs can allow attackers to inject malicious data into smart contracts. Common validation issues include:
- Missing bounds checking on numerical inputs
- Insufficient validation of external contract addresses
- Improper handling of array lengths and indices
- Unchecked return values from external calls
Proper input validation is crucial for maintaining contract integrity and preventing manipulation of contract state.
Reentrancy attacks exploit a contract's ability to call external functions before completing its own state updates. Notable impacts include:
- The DAO hack of 2016 ($70M in losses)
- Multiple DeFi protocol exploits
- Cross-function reentrancy vulnerabilities
Prevention strategies include:
- Implementing the checks-effects-interactions pattern
- Using reentrancy guards
- Ensuring all state updates occur before external calls
When smart contracts fail to verify the success of external calls, they risk proceeding with incorrect assumptions about transaction outcomes. Critical issues include:
- Failure to check return values from low-level calls
- Improper handling of failed token transfers
- Unsafe assumptions about external contract behavior
- Callback function manipulation
Best practices include implementing proper error handling and using safe transfer patterns for all external interactions.
Flash loans are a unique DeFi feature that allows users to borrow funds without collateral, provided the loan is repaid within the same transaction block. While innovative, this mechanism can be exploited in several ways:
- Market manipulation through large-scale temporary borrowing
- Draining liquidity pools through price manipulation
- Exploiting arbitrage opportunities across multiple DeFi protocols
These attacks have become increasingly sophisticated, often combining multiple vulnerabilities for maximum impact.
Arithmetic errors occur when calculations exceed data type limits, potentially allowing attackers to manipulate balances or bypass restrictions. Common scenarios include:
- Token balance manipulation through overflow in transfer functions
- Bypassing maximum supply limits through arithmetic wraparound
- Exploiting underflow in subtraction operations to create large balances
While modern Solidity versions include SafeMath by default, many legacy contracts remain vulnerable.
Blockchain's deterministic nature makes generating secure randomness challenging. This vulnerability affects:
- Gambling and lottery smart contracts
- Random token distribution mechanisms
- NFT minting sequences
Predictable randomness can be exploited by attackers who can calculate outcomes in advance, compromising the fairness of these systems. Solutions often require external sources of entropy or verifiable random functions (VRFs).
DoS attacks in smart contracts target resource-intensive functions, making them unusable by:
- Exhausting gas limits through complex loops or calculations
- Blocking critical contract functions through state manipulation
- Creating resource bottlenecks in external calls
These attacks can render contracts temporarily or permanently unusable, potentially trapping funds or disrupting essential services. Proper gas optimization and fail-safe mechanisms are essential for prevention.
| Rank | Vulnerability | Description | Impact |
|---|---|---|---|
| 1 | Access Control Vulnerabilities | Weaknesses in access control mechanisms that allow unauthorized access to resources or functionality. Led to $953.2M in losses (2024). | Critical |
| 2 | Price Oracle Manipulation New | Exploitation of price feed mechanisms to manipulate asset valuations and trigger malicious trades | Critical |
| 3 | Logic Errors | Business logic flaws leading to improper token minting, flawed lending protocols, or incorrect reward distributions. ($63M in losses) | High |
| 4 | Lack of Input Validation New | Insufficient validation of user input leading to various injection attacks and data corruption | High |
| 5 | Reentrancy Attacks | Vulnerabilities allowing attackers to repeatedly call functions before previous executions complete. Notable: DAO hack ($70M) | Critical |
| 6 | Unchecked External Calls | Insecure handling of external contract calls and API interactions leading to inconsistent states | High |
| 7 | Flash Loan Attacks New | Exploitation of flash loan mechanisms to manipulate markets or drain liquidity pools | Critical |
| 8 | Integer Overflow and Underflow | Arithmetic operation errors leading to balance manipulation or restriction bypasses | High |
| 9 | Insecure Randomness | Predictable randomness compromising lotteries, token distributions, and other random-dependent functions | High |
| 10 | Denial of Service (DoS) Attacks | Resource exhaustion attacks targeting gas limits or computational resources | High |
Based on incidents documented in SolidityScan's Web3HackHub and Immunefi's Crypto Losses Report, these vulnerabilities continue to pose significant risks to blockchain applications. Organizations must prioritize security measures and regular audits to protect against these emerging threats.