OWASP Top 10 Web Application Security Risks
The OWASP Top 10 is a standard awareness document for developers and web application security. It represents a broad consensus about the most critical security risks to web applications. This list is updated every few years to reflect the evolving threat landscape and emerging vulnerabilities.
Evolution from 2021 to 2025
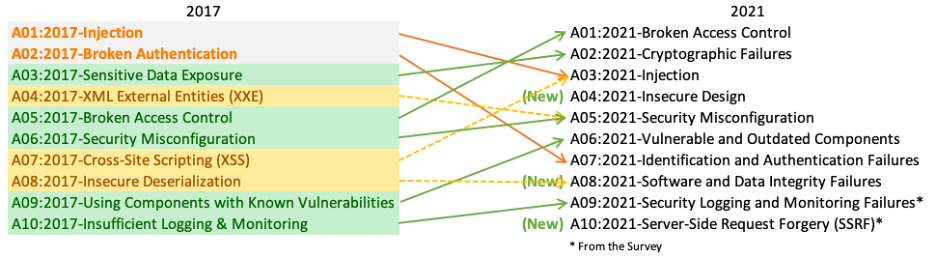
REMOVED XML External Entities (XXE), Insecure Deserialization
2021 Impact Statistics
0
Vulnerability Prevalence
94% of applications tested0
Average CVSS Score
Critical vulnerabilities0
Median Time to Fix
2.7 months0
Average Vulnerabilities
Per applicationBroken access control moves up from the fifth position to the category with the most serious web application security risk. The 34 CWEs mapped to Broken Access Control had more occurrences in applications than any other category.
Example: Accessing other users' accounts, viewing sensitive files, modifying other users' data, changing access rights.
Cryptographic failures, previously known as "Sensitive Data Exposure," focus on failures related to cryptography which often lead to exposure of sensitive data.
- Weak encryption algorithms
- Insecure key management
- Missing encryption of sensitive data
Injection slides down to the third position. 94% of the applications were tested for some form of injection with a max incidence rate of 19%, an average incidence rate of 3%, and 274k occurrences.
- SQL Injection
- NoSQL Injection
- Command Injection
- LDAP Injection
Insecure Design is a new category for 2021, focusing on risks related to design and architectural flaws. Many applications with secure code are deployed insecurely due to insecure design.
- Missing threat modeling
- Insecure architecture patterns
- Lack of security controls
Security misconfiguration moves up from #6 in the previous edition. 90% of applications were tested for some form of misconfiguration, with an average incidence rate of 4.5%.
- Default configurations
- Unnecessary features enabled
- Insecure cloud configurations
- Missing security headers
Vulnerable and Outdated Components was previously titled "Using Components with Known Vulnerabilities" and is #2 in the Top 10 community survey, but also had enough data to make the Top 10 via data analysis.
- Unpatched systems
- Outdated dependencies
- Unsupported software
Identification and Authentication Failures was previously "Broken Authentication" and is sliding down from the second position, and now includes CWEs that are more related to identification failures.
- Weak password policies
- Session management flaws
- Credential stuffing
- Multi-factor authentication bypass
Software and Data Integrity Failures is a new category for 2021, focusing on making assumptions related to software updates, critical data, and CI/CD pipelines without verifying integrity.
- Insecure deserialization
- Supply chain attacks
- Untrusted data sources
Security Logging and Monitoring Failures was previously "Insufficient Logging & Monitoring" and is added from the Top 10 community survey (#3), moving up from #10 previously.
- Missing audit logs
- Insufficient monitoring
- Log tampering
- Alert fatigue
Server-Side Request Forgery (SSRF) is a new category for 2021. The data shows a relatively low incidence rate with above average testing coverage, along with above-average ratings for Exploit and Impact potential.
- Internal network scanning
- Cloud metadata attacks
- Local file inclusion
| Rank | Vulnerability | Description | Impact |
|---|---|---|---|
| 1 | Broken Access Control | Restrictions on what authenticated users are allowed to do are often not properly enforced. | Critical |
| 2 | Cryptographic Failures | Failures related to cryptography which often lead to exposure of sensitive data. | Critical |
| 3 | Injection | User-supplied data is not validated, filtered, or sanitized by the application. | Critical |
| 4 | Insecure Design New | Flaws in design and architecture that cannot be fixed by proper implementation. | High |
| 5 | Security Misconfiguration | Improperly configured permissions on cloud services, unnecessary features enabled. | High |
| 6 | Vulnerable Components | Using components with known vulnerabilities undermines application defenses. | High |
| 7 | Auth Failures | Confirmation of the user's identity, authentication, and session management. | High |
| 8 | Software and Data Integrity Failures New | Software and data integrity failures relate to code and infrastructure that does not protect against integrity violations. | High |
| 9 | Logging Failures | Insufficient logging and monitoring coupled with missing or ineffective integration with incident response. | High |
| 10 | SSRF New | Server-Side Request Forgery flaws occur when a web application is fetching a remote resource without validating the user-supplied URL. | High |
The OWASP Top 10 is based on a consensus of security experts from around the world. The risks are ranked by exploitability, detectability, and impact. Organizations should use this list to understand the most critical web application security risks and take appropriate measures to protect their applications.